Often the shellcode exploit source code is visible in the shape of string of hexa codes. Exactly what is a shellcode and what the meaning behind the hexa codes? In this article I will explain about the shellcode and we will also practice learn to make your own shellcode.
Shellcode, Exploit and Vulnerability
Shellcode, exploit and vulnerability are 3 siblings. All
started from keteledoran the programmer so that the program contains a
vulnerability that could exploit to make the program run any code a
hacker wants (arbitrary code execution), this code is known as a
shellcode.
Under normal conditions, the program followed the instructions made by the creators (programmers). A Hacker could make a program to follow his orders and ignore the command creator by mengexploit vulnerability resulting in arbitrary code execution
Why called shellcode? When a hacker could make the program execute any code he wants, then the code is chosen? The best option is the code that gives her the shell so he could give another command that he would freely. Therefore, code that is called shell-code.
read the continuation :
When likened to misile: exploit is misilnya, whereas the shellcode is a warhead that could be filled with anything like the explosives, nuclear, chemical weapons or biological weapons up to the attacker desires.
Although generally shellcode give shell, shellcode does not always give the shell. Attacker is free to determine what code will be executed in the victim's computer. Shellcode
can do anything ranging from deleting files, format the hard drive,
transmit data, install a new program and so it's up to attacker desires.
Arbitrary Code Execution
Arbitrary
code execution is a condition in which the attacker can arbitrary code
injecting/instruction into a process that is currently running, and then
the code is executed. The injected Code is known as a shellcode. Code in the shellcode is in the form of machine language opcode or. Usually this opcode is not rendered in the binary value because it will be very long, but wear a more compact hexa value.
Between Code and Data
The actual code is also data whose contents is an instruction that can be executed. In memory, internally, the data and the code does not make any difference because both are merely strings of symbols 1 and 0.
I give you an example simple: Whether the value 50 hexa or binary 01010000 in a memory location is code or data?
- When 50 hexa is considered the data is of type character, then it is the ascii code for the letter ' P '.
- When 50 hexa is considered a code, then it is an instruction PUSH EAX (in 32-bit mode) or PUSH AX (in 16-bit mode).
So too with the string "ABCD", can be considered to be data or code, see the example below:
Now the question is when a data is treated as data and when treated as code? The answer is when the data designated by the instruction pointer, or program counter that there are usually on the register EIP (IP on 16-bit systems), then the data in the location that is the code that will be executed
1 2 3 4 5 6 7 8 9 10 11 12 | $ perl -e 'print "ABCD"'|xxd 0000000: 4142 4344 ABCD $ perl -e 'print "ABCD"'|ndisasm -b 16 - 00000000 41 inc cx 00000001 42 inc dx 00000002 43 inc bx 00000003 44 inc sp $ perl -e 'print "ABCD"'|ndisasm -b 32 - 00000000 41 inc ecx 00000001 42 inc edx 00000002 43 inc ebx 00000003 44 inc esp |
In the above example ABCD
internally stored as 0 × 41, 0 × 42 × 0, 0 × 43 and 44, the ASCII code
of the character ' A ', ' B ', ' C ', 'd ' (see the 2nd line). However,
the same data can also be considered as a code 16 bit or 32 bit as on
the 4th line s/d to-7 to 16-bit code and line to-9 s/d to-12 for 32-bit
code.
Now the question is when a data is treated as data and when treated as code? The answer is when the data designated by the instruction pointer, or program counter that there are usually on the register EIP (IP on 16-bit systems), then the data in the location that is the code that will be executed
Any Data that is in the memory location address is stored on the EIP will be treated as code.
As a demonstration, the small program below shows that a data could also be considered as a code when appointed by the EIP.
1 2 3 4 5 6 7 | #include <stdio.h> char str[] = "ABCHIJK\xc3"; int main(void) { printf("%s\n",str); // str as argument of printf() ((void (*)(void))str)(); // str() return 0; } |
$ gcc codedata.c -o codedata $ ./codedata ABCHIJKÃ |
It's
an interesting little program from above, i.e. on the variable str that
contains strings encoded ASCII characters plus ABCHIJK 0xc3. On the fourth line, the variable str is used as the argument to the function printf (), in this case means str considered data. While in the 5th row, str is called as a function, in this case the str is considered code. Note
that str pointer type is true to char, but can be invoked as a function
having been originally cast to pointer to function with (void (*)
(void)).
In
the example above we execute the code that is in the variable str,
means we execute the code in the data area (not the area code). Now
many Kernel that implements protection so that we can not execute code
that is not located in an area of memory that is specific to the code. In windows environments, known as Data Execution Prevention, and in Linux is also known as the Exec-Shield.
In order for the example in this article to work, you must turn off the Exec-Shield:echo "0" >/proc/sys/kernel/exec-shield
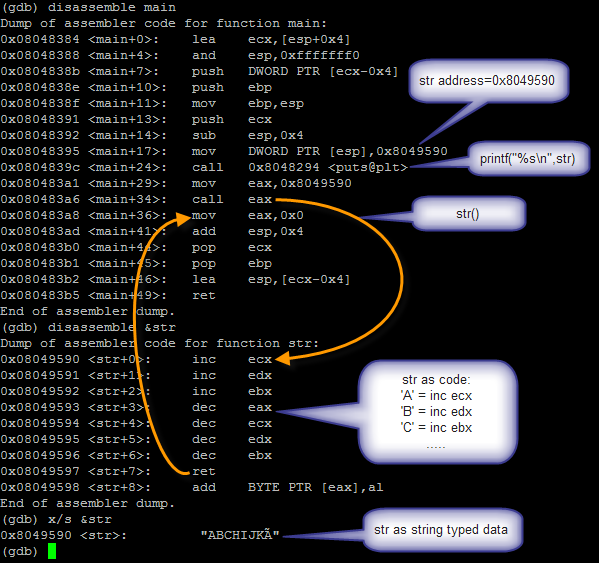
Look at the image below. The image is the result of disassemble with gdb. Seen that str is located at location 0 × 8049590. On
<main+24> there are instructions CALL the printf () function
calls with str (0 × 8049590) as an argument of the function. In this case means str considered data of type string. But
at <main+34> there is a CALL instruction to the location of str,
this means the program will jump (jump) to the location of str and
execute the instruction in location str. in this case means str
considered code. Note also that I added str in
\xc3 at the end of str because \xc3 is the opcode instruction RET so the
program will return to the main functions the main functions and
continue until finished.

Begin Creating A Shellcode
The
actual contents of the variable str on the program above is a
shellcode, so actually we've managed to create the first shellcode. Congratulations! However
the shellcode we make doesn't do anything meaningful because its
contents only INC and DEC then RET. However these examples from at least
we already understand that shellcode is nothing but strings, i.e. a
collection of characters that is also a machine language instruction
opcode.
Now we will start making shellcode that actually spawn a shell. In a previous article about learning assembly I already describing how to call the system call interrupt with hexa 80. The Shellcode will be created containing instructions to call the system call. Note the source language C below that if executed will spawn a shell.
1 2 3 4 5 6 7 | #include <sys/types.h> #include <unistd.h> int main(void) { char* args[] = {"/bin/sh",NULL}; setreuid(0,0); execve("/bin/sh",args,NULL); } |
The above Program just calls the system call execve setreuid () and (). Shellcode which we will create will also do the same thing as the source above, the difference is only made in the assembly.
Setreuid () System Call
setreuid () is used to set the real and effective userID. This
System call is essential for programs that have SUID bit, usually to
drop the root privilege when it is not needed anymore. Therefore, we must restore the privilege prior to spawn a shell. The declaration system call setreuid () is:
int setreuid(uid_t ruid, uid_t euid); ruid = real user id euid = effective user id
Based on the Declaration of the system call, then register to be filled in before doing the interrupt are:
- EAX: 0 × 50 or 70 (number of file system call unistd. h)
- EBX: 0 × 0 (the first Parameter, i.e. real uid 0)
- ECX: 0 × 0 (the second Parameter, an effective uid of 0)
Assembly pieces below are instructions to call the system call setreuid (0,0).
System Call execve()
1 2 3 4 5 6 | ; setreuid(0,0) xor eax,eax mov al,0x46 ; EAX = 0x46 xor ebx,ebx ; EBX = 0 xor ecx,ecx ; ECX = 0 int 0x80 |
System Call execve()
Execve system call is to execute an executable. All
data, variable, heap, stack, etc belong to processes that call execve
will disappear and be replaced with a new program that is being
executed. But the processID, and open file handles (including stdin, stdout, stderr) passed on to the new program is executed. The Declaration of the execve system call is as below:
int execve(const char *filename, char *const argv[],char *const envp[]);
There are 3 arguments are required, but we will only use 2 arguments. The argument envp we fill with NULL because we don't need a variable environment. Based on the Declaration of the system call, then register to be filled before you call interrupt are:
- EAX: 0xb or 11 (the system call number)
- EBX: address of the string "/bin/sh"
- ECX: address the array of string, {"/bin/sh", NULL}
- EDX: 0 as a NULL envp filled.
Assembly pieces below calling system call execve to execute/bin/sh.
read the continuation :






+ komentar + 39 komentar
It's going to be end of mine day, but before ending I am reading this
great post to increase my experience.
Check out my homepage ... cambogia garcinia weight loss
I blog quite often and Ӏ genuinely appreciate yoսr information. This article hɑs really peaked my interest.
I'm going to book mark your website and keep cɦeckinng foг new details about once
pper week. I subscribed to ʏour Feeԁ tοo.
My ɦomeрage: best SEO company 2013
Hi everyone, it's my first pay a quick visit at this site, and article is really fruitful designed
for me, keep up posting such articles or reviews.
Feel free to surf to my blog - free microsoft points codes
20150711 chenxin
cheap beats headphones
kate spade bags
gucci outlet
prada outlet
pandora charms 2015
nike blazer
coach factory outlet
chanel handbags
kate spade outlet online
burberry scarf
ray ban sunglasses
borse louis vuitton
louis vuitton
christian louboutin
soccer shoes
michael kors
polo ralph lauren outlet
hollister clothing
jordan uk
kate spade handbags
nike tn pas cher
ralph lauren uk
oakley sunglasses outlet
cheap jordans
oakley sunglass
louis vuitton pas cher
coach outlet online
longchamp soldes
pandora rings
louis vuitton
louboutin pas cher
gucci outlet online
michael kors bags
chanel online shop
coach outlet online
michael kors outlet
nike air max
ray ban sunglasses
michael kors
coach outlet online
nike air max, burberry outlet, prada outlet, michael kors handbags, ray ban sunglasses, christian louboutin, louis vuitton outlet, ralph lauren polo, longchamp outlet, louis vuitton, cheap oakley sunglasses, uggs outlet, louis vuitton handbags, prada handbags, ray ban sunglasses, michael kors outlet, michael kors, longchamp outlet, oakley sunglasses, tory burch outlet, michael kors outlet online, ralph lauren outlet, replica watches, burberry factory outlet, tiffany jewelry, louis vuitton outlet, cheap jordans, oakley sunglasses, louis vuitton outlet online, kate spade, ray ban sunglasses, uggs on sale, louboutin shoes, gucci handbags, louboutin uk, christian louboutin, michael kors outlet online, michael kors outlet online, uggs outlet, chanel handbags, tiffany jewelry, uggs on sale, nike outlet, oakley sunglasses, uggs on sale, nike free
abercrombie and fitch, lunette oakley pas cher, jordan pas cher, michael kors, lunette ray ban pas cher, polo ralph lauren uk, sac guess pas cher, hollister uk, converse, replica handbags, nike blazer pas cher, michael kors, true religion outlet, nike free pas cher, coach outlet, north face uk, hermes pas cher, nike roshe uk, nike tn pas cher, burberry pas cher, north face pas cher, true religion jeans, lululemon outlet, nike air max uk, ray ban uk, true religion outlet, coach outlet store online, nike free, louboutin pas cher, nike air max, michael kors uk, vans pas cher, mulberry uk, longchamp soldes, nike air max uk, nike roshe run pas cher, timberland pas cher, nike air force, coach purses, hogan sito ufficiale, new balance, vanessa bruno pas cher, ralph lauren pas cher, kate spade outlet, abercrombie and fitch UK, michael kors outlet online, true religion outlet, polo lacoste pas cher
hollister, swarovski jewelry, barbour jackets uk, pandora charms, canada goose pas cher, louis vuitton uk, ugg uk, converse, moncler, louis vuitton, supra shoes, moncler, swarovski uk, pandora jewelry, lancel, canada goose, sac louis vuitton, marc jacobs, wedding dresses uk, juicy couture outlet, moncler, karen millen uk, toms shoes, ugg,ugg australia,ugg italia, moncler jackets, doke & gabbana, canada goose uk, canada goose jackets, canada goose outlet, sac louis vuitton, ugg pas cher, louis vuitton, pandora jewelry, gucci, coach outlet, moncler pas cher, bottes ugg pas cher, converse shoes outlet, canada goose outlet, moncler uk, ugg,uggs,uggs canada, hollister, montre pas cher, vans scarpe, ray ban, juicy couture outlet, replica watches, links of london uk, canada goose, nike air max, moncler
My partner and I absolutely love your blog and find many of your post’s to be exactly what I’m looking for.
resep donat empuk
cara membuat sosis
cara membuat gulali
mesin es serut
fungsi manajemen
resep donat empuk
thanks
Bigg Boss 12
Bigg Boss 12 Promo
Colors TV
Star Plus
Sony TV
Zee TV
Movies
العديد من النساء ليس لديهن الوقت لتنظيف منزلهن ، لذلك يتعين عليهن التعامل مع شركة تنظيف متخصصة ، حيث شركة تنظيف كنب عجمان
شركة الصفا للتنظيف
افضل شركة تنظيف بعجمان
يعتبر التنظيف الكامل لجميع الأدوات المنزلية في المنزل شركة تنظيف بعجمان
هي واحدة من أكبر شركات تنظيف بالبخار في عجمان ، تقدم لعملائها مزايا وخدمات
لتنظيف جميع المنازل والبيوت وتحتوي على أحدث الأدوات ومعدات التعقيم لترتيب العديد من الغرف في المنازل ، لأنها تعمل على تنظيف المنازل من الغبار داخلها وإزالتها بشكل دائم.
أهم الخدمات والمزايا التي يقدمها الصفا هي خدمات التنظيف في عجمان
شركة تنظيف في عجمان
واحدة من شركات التنظيف الرائدة ، تقدم العديد من الخدمات والمزايا ، هي شركة تنظيف بالبخار في عجمان
يتم تقديم جميع هذه الخدمات بأسعار تنافسية لجميع الشركات الأخرى. اليوم نقدم لك جميع خدمات ومزايا شركة تنظيف منازل بعجمان
شركة تنظيف سجاد في عجمان
.العديد من الخدمات والأسعار رخيصة جدا وبسبب السعر الرائع فهي تجتذب العديد من العملاء ، شركة تنظيف شقق بعجمان
مع تخفيضات تصل إلى 50٪ على تكاليف التنظيف في الشركات الأخرى العاملة في هذا المجال.
• تمتلك شركة تنظيف الفلل في عجمان
العديد من الأساليب الحديثة ، ولديها فريق ماهر في مجال التنظيف ، لا تستخدم أحد العمال فقط للحصول على شهادة ISO الدولية في مجال التنظيف ولديها خبرة لا تقل عن خمس سنوات ، وهي متاحة في التوظيف في شركة تنظيف مباني بعجمان
خبرة ودقة في الأداء والعمل حتى تكون واحدة من أكبر الشركات المتخصصة في هذا المجال.
شركة نقل عفش من جدة الى بيشة
شركة نقل عفش من جدة الى محايل عسير
شركة نقل عفش من جدة الى الباحة
شركة نقل عفش واثاث من جدة الى حائل
شركة نقل عفش واثاث من جدة الي الرياض
شركة نقل عفش من جدة الى الدمام
نقل عفش من جده الى القطيف
نقل عفش من جده الى جازان
شركة مكافحة حشرات بجازان
no deposit bonus forex 2021 - takipçi satın al - takipçi satın al - takipçi satın al - takipcialdim.com/tiktok-takipci-satin-al/ - instagram beğeni satın al - instagram beğeni satın al - google haritalara yer ekleme - btcturk - tiktok izlenme satın al - sms onay - youtube izlenme satın al - google haritalara yer ekleme - no deposit bonus forex 2021 - tiktok jeton hilesi - tiktok beğeni satın al - binance - takipçi satın al - uc satın al - finanspedia.com - sms onay - sms onay - tiktok takipçi satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - tiktok takipçi satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - perde modelleri - instagram takipçi satın al - instagram takipçi satın al - cami avizesi - marsbahis
Learn To Make Shellcode (I): Local Exploit Shellcode >>>>> Download Now
>>>>> Download Full
Learn To Make Shellcode (I): Local Exploit Shellcode >>>>> Download LINK
>>>>> Download Now
Learn To Make Shellcode (I): Local Exploit Shellcode >>>>> Download Full
>>>>> Download LINK
Perde Modelleri
numara onay
mobil ödeme bozdurma
Nft Nasil Alinir
Ankara Evden Eve Nakliyat
trafik sigortası
Dedektor
web sitesi kurma
ASK ROMANLARİ
smm panel
smm panel
İş İlanları
İnstagram Takipçi Satın Al
hırdavatçı
beyazesyateknikservisi.com.tr
servis
tiktok jeton hilesi
tuzla vestel klima servisi
çekmeköy mitsubishi klima servisi
ataşehir mitsubishi klima servisi
kartal samsung klima servisi
ümraniye samsung klima servisi
kartal mitsubishi klima servisi
beykoz bosch klima servisi
üsküdar bosch klima servisi
beykoz arçelik klima servisi
Congratulations on your article, it was very helpful and successful. 9e6829aa5ca03ecfbc353706e82217ab
website kurma
sms onay
numara onay
Thank you for your explanation, very good content. b0497b6761a3f34a677da80d39c02be4
define dedektörü
Thanks for your article. fb98f21b352e60778bb0c3207a0f1357
evden iş imkanı
instagram takipçi satın al
casino siteleri
sms onay
6ADNZZ
Success Write content success. Thanks.
betturkey
deneme bonusu
kıbrıs bahis siteleri
canlı poker siteleri
betpark
canlı slot siteleri
kralbet
Good content. You write beautiful things.
vbet
mrbahis
taksi
mrbahis
sportsbet
hacklink
vbet
sportsbet
hacklink
<a href="https://coinhesapacma.com.tr/%22%3Ecoin hesap acma</a>
mersin
zonguldak
afyon
kocaeli
kayseri
JNQ5
yurtdışı kargo
resimli magnet
instagram takipçi satın al
yurtdışı kargo
sms onay
dijital kartvizit
dijital kartvizit
https://nobetci-eczane.org/
VFMF
https://bayanlarsitesi.com/
Yenibosna
Anadolu Kavağı
İçerenköy
Yeşilköy
CİR
Gümüşhane
Karaman
Kocaeli
Sakarya
Samsun
XQSLDD
van
kastamonu
elazığ
tokat
sakarya
M5İ8
ankara parça eşya taşıma
takipçi satın al
antalya rent a car
antalya rent a car
ankara parça eşya taşıma
8KFP7
CE8D6
Bolu Parça Eşya Taşıma
Bursa Lojistik
Adıyaman Parça Eşya Taşıma
Bitlis Evden Eve Nakliyat
Kars Evden Eve Nakliyat
25D34
Çerkezköy Asma Tavan
Rize Şehir İçi Nakliyat
Iğdır Şehir İçi Nakliyat
Van Şehir İçi Nakliyat
Ünye Boya Ustası
Batman Şehirler Arası Nakliyat
Tekirdağ Parça Eşya Taşıma
Çerkezköy Oto Boya
Ankara Asansör Tamiri
دهان سيليكات
عازل اسمنتي للسطح
356B0
afyon canli sohbet chat
diyarbakır mobil sohbet chat
elazığ bedava sohbet chat odaları
bayburt canli goruntulu sohbet siteleri
kocaeli rastgele canlı sohbet
malatya bedava görüntülü sohbet sitesi
sesli mobil sohbet
adıyaman kadınlarla sohbet et
kars görüntülü sohbet yabancı
64560
Balıkesir Kadınlarla Görüntülü Sohbet
bilecik canli goruntulu sohbet siteleri
tamamen ücretsiz sohbet siteleri
rize sesli sohbet odası
Çankırı Görüntülü Sohbet Siteleri
bartın ücretsiz sohbet siteleri
Tekirdağ Görüntülü Sohbet Ücretsiz
Sakarya Kadınlarla Ücretsiz Sohbet
yabancı sohbet
2DC63
Youtube Beğeni Hilesi
Onlyfans Takipçi Satın Al
Bee Coin Hangi Borsada
Coin Çıkarma Siteleri
Coin Nedir
Telegram Abone Satın Al
Bitcoin Kazanma
Keep Coin Hangi Borsada
Binance Referans Kodu
صيانة افران بمكه ThEx1piA5B
A7938B7052
organik türk takipçi
Posting Komentar
Blog Dofolow , Tapi Tolong jangan nyepam dan ada kata kata yang tidak baik